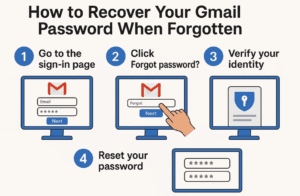
Forgetting your Gmail password can be frustrating, but don’t worry—Google provides multiple ways to recover your account. In this guide, we’ll walk you through step-by-step methods to regain access to your Gmail account, whether...
Read More
How to Use Hydra for Brute Force Attacks on Metasploitable Using the CLI
⚠️ Disclaimer: This article is intended for educational purposes and ethical hacking only. Always ensure you have permission before attempting any penetration test. Hydra is one of the most widely used tools for performing...
Read More
Understanding Password Hashing and How to Protect Your Accounts Online
In the world of cybersecurity, protecting your password is critical. With data breaches becoming more frequent, understanding how passwords are stored and how attackers attempt to crack them is essential for both individuals and...
Read More
Understanding Hashing and Encryption: A Beginner-Friendly Guide
In today’s digital age, security and privacy are top priorities. Whether you’re creating an online account or sending confidential messages, cryptographic concepts like hashing and encryption play a crucial role in safeguarding your data....
Read More