Once upon a time, the internet was peaceful.You could open a website, read an article, and not be bombarded with pop-ups, auto-playing videos, and floating “Subscribe Now” banners chasing you like digital mosquitoes. Fast...
Read More
🛜 Can the Owner of an Open Wi-Fi Hotspot See What Files You’re Downloading?
Public Wi-Fi networks are convenient — they’re available in cafes, airports, hotels, and even shopping malls. But have you ever stopped to wonder whether the person providing that Wi-Fi can actually see what you’re...
Read More
⚙️ Cudy R700 Configuration Made Easy: Step-by-Step Setup, Load Balancing, and Performance Guide
Setting up a dual WAN router might sound complicated, but the Cudy R700 makes it surprisingly easy — even for home users. Designed for small offices, gamers, and professionals who need network stability, this...
Read More
⚡ Complete Setup and Configuration Guide for Cudy WR11000 Wi-Fi 7 Tri-Band Router
Setting up a high-performance router like the Cudy WR11000 can truly transform your internet experience — but only if it’s configured correctly. This router supports Wi-Fi 7 with 2.4GHz, 5GHz, and 6GHz tri-band connectivity,...
Read More
🔒 How to Block a Program from Accessing the Internet on Windows 11 Using Windows Defender Firewall
In today’s connected world, almost every program installed on your computer communicates with the internet — whether for updates, analytics, license verification, or background data sync. While this is often harmless, there are legitimate...
Read More
Step-by-Step Guide to Add a Free VPN Without Any Software
How to Set Up a Free VPN in Windows 10 Using VPNBook Step-by-Step Guide to Add a Free VPN Without Any Software Using a VPN (Virtual Private Network) is one of the easiest ways...
Read More
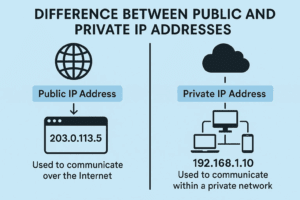
Understanding the Difference Between Public and Private IP Addresses (IPv4)
When connecting to the internet or setting up a network, you might come across the terms public IP address and private IP address. While they might sound similar, they serve very different purposes in...
Read More
10 Pieces of Bad Cybersecurity Advice You Should Ignore
Cybersecurity is a critical topic, but not all advice floating around the internet is worth following. In fact, some commonly repeated tips can actively make you less secure. This article breaks down ten of...
Read More
Understanding Kali Linux and Its Role in White Hat Hacking
Many of you have often asked me questions about Kali Linux — what it is, and how it is used, especially in the field of ethical hacking.Today, in this article, we’ll dive deep into...
Read More
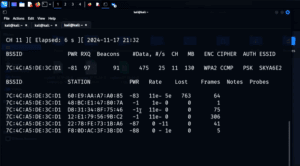
How to Capture and Crack a WPA Handshake Using Aircrack-ng (For Educational Purposes Only)
⚠️ Disclaimer: This technique is intended strictly for educational and ethical penetration testing purposes. It should never be used on public networks or without explicit permission. Always ensure you are working in a controlled...
Read More
How to Perform Reconnaissance and Vulnerability Testing Using Nikto and Nmap
In the world of cybersecurity and penetration testing, two tools stand out for their usefulness in performing reconnaissance and vulnerability assessments: Nikto and Nmap. Whether you’re a budding ethical hacker or a seasoned IT...
Read More
How to Perform Wi-Fi Penetration Testing Using Fern and Wifite on Kali Linux
Disclaimer:This article is intended strictly for educational purposes only. The tools and techniques described here are designed for ethical hacking and cybersecurity learning. Never attempt unauthorized access to any network you do not own...
Read More
Introduction to BetterCAP: The Swiss Army Knife for Network Penetration Testing
Disclaimer: This article is for educational purposes only. The techniques and tools described should never be used on public networks or without proper authorization. Always ensure your actions comply with applicable laws and ethical...
Read More
How to Demonstrate FTP Vulnerabilities Using Wireshark (For Educational Purposes Only)
Disclaimer: This article is for educational purposes only. Do not attempt any of the procedures outlined here on systems or servers without explicit permission from the owner. Always conduct cybersecurity tests within legal boundaries...
Read More
How to View Your Connected Wi-Fi Password on an Android Phone (No Root Needed)
Ever needed to connect another device to your Wi-Fi but couldn’t remember the password? Good news — you can view your connected Wi-Fi password directly from your Android phone without rooting your device or...
Read More