For many people who work in cybersecurity, digital forensics, and ethical hacking, having the right tools at the right time can make all the difference. Whether you’re conducting a penetration test, analyzing a compromised...
Read More
🐧 Just 10 Minutes Read: Every Major Linux Distro Explained (2025 Guide)
Linux isn’t just one operating system—it’s an entire family of operating systems (called distributions or distros) that serve different kinds of users. Some are built for beginners who just want an easy alternative to...
Read More
How to Perform a Clean Installation of Kali Linux on a Laptop or PC (2025 Guide)
If you’re looking to install the latest version of Kali Linux (2025.1) on your laptop or desktop, you’ve come to the right place. This article walks you through the complete process step by step...
Read More
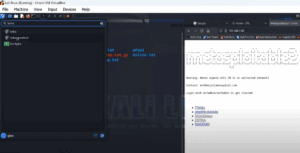
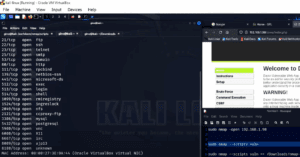
How to Set Up Kali Linux and Metasploitable 2 on VirtualBox (Beginner-Friendly Guide)
Setting up a penetration testing environment on your personal computer is a great way to learn cybersecurity and ethical hacking. This article will walk you through a complete beginner-friendly setup of Kali Linux and...
Read More
How to Run Linux on Windows Using WSL (Windows Subsystem for Linux)
Running Linux on your Windows PC has never been easier, thanks to WSL (Windows Subsystem for Linux). If you’re a developer, power user, or tech enthusiast who wants to explore Linux without setting up...
Read More
How to Download and Install Kali Linux on VMware Workstation (Step-by-Step Guide)
If you’re planning to use Kali Linux for penetration testing or cybersecurity practice, setting it up inside a virtual machine is a smart choice. In this detailed guide, you will learn how to easily...
Read More
How to Download and Install Kali Linux on VirtualBox: A Step-by-Step Guide for Beginners
Are you interested in setting up Kali Linux on your system using VirtualBox but unsure where to start? No worries! This beginner-friendly guide will walk you through every step clearly and simply. Even if...
Read More
How to Install Kali Linux on Your PC or Laptop: Step-by-Step Guide
If you’re looking to install Kali Linux on your PC or laptop, you’re in the right place. This article will guide you through the entire process, from downloading the necessary files to setting up...
Read More
Understanding Kali Linux and Its Role in White Hat Hacking
Many of you have often asked me questions about Kali Linux — what it is, and how it is used, especially in the field of ethical hacking.Today, in this article, we’ll dive deep into...
Read More
Kali Purple: 20 Essential Post-Installation Steps for Optimal Security
Introduction Kali Purple marks a major evolution in cybersecurity tools—shifting from Kali Linux’s offensive security focus to a defensive security powerhouse. Designed for blue teams, SOC analysts, and cybersecurity defenders, Kali Purple provides an...
Read More
Kali Purple: The Ultimate Defensive Security OS – Tools & Techniques Revealed
The cybersecurity landscape is evolving, and Kali Purple has emerged as a game-changer—shifting from offensive penetration testing to proactive cyber defense. Built by the creators of Kali Linux, this new distro is packed with...
Read More
How to Use Hydra for Brute Force Attacks on Metasploitable Using the CLI
⚠️ Disclaimer: This article is intended for educational purposes and ethical hacking only. Always ensure you have permission before attempting any penetration test. Hydra is one of the most widely used tools for performing...
Read More
A Step-by-Step Guide to Nmap Vulnerability Scanning Using NSE Scripts
⚠️ Disclaimer: This guide is intended strictly for ethical hacking and penetration testing in controlled environments with explicit permission. Do not attempt this on unauthorized systems. When it comes to penetration testing, simply identifying...
Read More
Introduction to Shodan: The Search Engine for Internet-Connected Devices
In the world of cybersecurity and ethical hacking, Shodan is an incredibly powerful tool used to identify and analyze devices that are publicly accessible on the internet. From smart homes and business networks to...
Read More
Understanding Password Hashing and How to Protect Your Accounts Online
In the world of cybersecurity, protecting your password is critical. With data breaches becoming more frequent, understanding how passwords are stored and how attackers attempt to crack them is essential for both individuals and...
Read More
How to Install Kali Linux on a USB Flash Drive: A Step-by-Step Guide
Disclaimer:This article is intended for educational purposes only. The tools and techniques discussed here should only be used ethically and legally, never for any malicious or unauthorized activity. Installing Kali Linux on a USB...
Read More
How to Perform Wi-Fi Penetration Testing Using Fern and Wifite on Kali Linux
Disclaimer:This article is intended strictly for educational purposes only. The tools and techniques described here are designed for ethical hacking and cybersecurity learning. Never attempt unauthorized access to any network you do not own...
Read More
Introduction to BetterCAP: The Swiss Army Knife for Network Penetration Testing
Disclaimer: This article is for educational purposes only. The techniques and tools described should never be used on public networks or without proper authorization. Always ensure your actions comply with applicable laws and ethical...
Read More
How to Demonstrate FTP Vulnerabilities Using Wireshark (For Educational Purposes Only)
Disclaimer: This article is for educational purposes only. Do not attempt any of the procedures outlined here on systems or servers without explicit permission from the owner. Always conduct cybersecurity tests within legal boundaries...
Read More
How to Test Wi-Fi Security Using Fern WiFi Cracker: A Beginner’s Guide to Ethical Hacking
Disclaimer: This article is intended strictly for educational and ethical hacking purposes. Do not attempt these techniques on any network that you do not own or have explicit permission to test. Unauthorized access to...
Read More