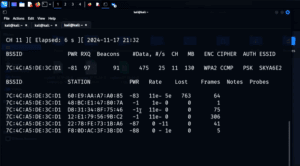
⚠️ Disclaimer: This technique is intended strictly for educational and ethical penetration testing purposes. It should never be used on public networks or without explicit permission. Always ensure you are working in a controlled...
Read More