Disclaimer:This article is intended for educational purposes only. The tools and techniques discussed here should only be used ethically and legally, never for any malicious or unauthorized activity. Installing Kali Linux on a USB...
Read More
How to Perform Wi-Fi Penetration Testing Using Fern and Wifite on Kali Linux
Disclaimer:This article is intended strictly for educational purposes only. The tools and techniques described here are designed for ethical hacking and cybersecurity learning. Never attempt unauthorized access to any network you do not own...
Read More
A Beginner’s Guide to Computer Networking: From IP Addressing to NAT
Have you ever wondered how computers communicate with each other across the globe? It might seem like magic, but in reality, it’s a well-orchestrated system known as computer networking—a complex yet fascinating field that...
Read More
Introduction to BetterCAP: The Swiss Army Knife for Network Penetration Testing
Disclaimer: This article is for educational purposes only. The techniques and tools described should never be used on public networks or without proper authorization. Always ensure your actions comply with applicable laws and ethical...
Read More
Understanding Hashing and Encryption: A Beginner-Friendly Guide
In today’s digital age, security and privacy are top priorities. Whether you’re creating an online account or sending confidential messages, cryptographic concepts like hashing and encryption play a crucial role in safeguarding your data....
Read More
How to Use SpiderFoot with GUI on Linux for Ethical Hacking and Vulnerability Scanning
SpiderFoot is a powerful open-source OSINT (Open Source Intelligence) tool used to automate the process of gathering information about IP addresses, domains, emails, and more. It’s perfect for penetration testers, cybersecurity professionals, and ethical...
Read More
How to Demonstrate FTP Vulnerabilities Using Wireshark (For Educational Purposes Only)
Disclaimer: This article is for educational purposes only. Do not attempt any of the procedures outlined here on systems or servers without explicit permission from the owner. Always conduct cybersecurity tests within legal boundaries...
Read More
Understanding Wi-Fi: How It Works and Why It’s So Important
Can you imagine a world without Wi-Fi? It’s hard to even picture it. From staying connected with friends to streaming your favorite shows, Wi-Fi is the invisible thread that holds our digital lives together....
Read More
How to Test Wi-Fi Security Using Fern WiFi Cracker: A Beginner’s Guide to Ethical Hacking
Disclaimer: This article is intended strictly for educational and ethical hacking purposes. Do not attempt these techniques on any network that you do not own or have explicit permission to test. Unauthorized access to...
Read More
How to Recover Google Account without Verification Code Password & Phone Number 2025
Losing access to your Gmail account—whether due to hacking or losing your device—can be incredibly stressful. If you no longer have access to your recovery phone number or email, don’t worry. This article explains...
Read More
How to Recover Your Gmail Account Without a Phone Number or Recovery Email
Losing access to your Gmail account can be incredibly frustrating—especially if you no longer have access to your recovery phone number or email address. Whether you’ve formatted your phone or simply don’t have those...
Read More
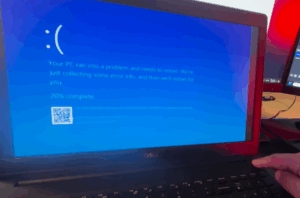
Fix Blue Screen of Death Caused by CrowdStrike Everywhere
A widespread issue is currently affecting Windows 10 and Windows 11 users across the globe. From television broadcasters to banks, airports, and supermarkets — many systems have been hit with the dreaded Blue Screen...
Read More
How to Maximize Your Windows Security Without Using Third-Party Antivirus
Welcome back, friends!If you’re someone who still uses Windows 7, 10, or 11, you might often wonder whether third-party antivirus software is necessary for complete protection. Based on extensive personal experience and testing, my...
Read More
Windows 11 vs Linux: Which One Is Best for You?
When it comes to choosing an operating system, most people default to what they already know — usually Windows. But in recent years, Linux has evolved into a strong contender, offering powerful features, customization,...
Read More
Beware of Sponsorship Email Scams: How Virtual Machines Can Save the Day
As a content creator on the internet, I frequently receive emails from various companies proposing sponsorships for my channel. Over time, reading these emails can lead to complacency, making it easier to overlook key...
Read More
A Comprehensive Look at Wuntu: A Windows-Like Linux Distro
For decades, Microsoft Windows has dominated the personal computing space, but its limitations and control over user customization have led some to seek alternatives. Many users dream of a Linux-based operating system that mimics...
Read More
13 Dangerous Android Malware Apps You Must Delete Immediately
In today’s digital age, safeguarding your smartphone against malware is critical. Cybercriminals often disguise harmful apps as useful tools to infiltrate your device, compromise your data, and jeopardize your security. Below is a detailed...
Read More
9. Securing Your WordPress Site
Security is crucial for protecting your WordPress site from threats like malware, hackers, and data breaches. This blog will guide you through essential steps to secure your site. 1. Keeping WordPress Updated Keeping your...
Read More