There are times when disabling Windows Defender becomes necessary. Perhaps you’re installing software that Windows Defender mistakenly flags as harmful, or you need to work with files that trigger constant warnings. In this article,...
Read More
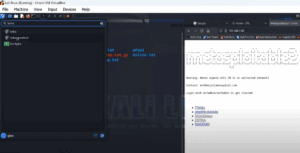
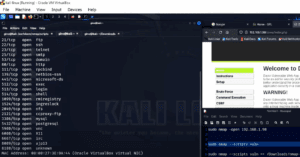
How to Download and Install Kali Linux on VMware Workstation (Step-by-Step Guide)
If you’re planning to use Kali Linux for penetration testing or cybersecurity practice, setting it up inside a virtual machine is a smart choice. In this detailed guide, you will learn how to easily...
Read More
Understanding Kali Linux and Its Role in White Hat Hacking
Many of you have often asked me questions about Kali Linux — what it is, and how it is used, especially in the field of ethical hacking.Today, in this article, we’ll dive deep into...
Read More
Kali Purple: 20 Essential Post-Installation Steps for Optimal Security
Introduction Kali Purple marks a major evolution in cybersecurity tools—shifting from Kali Linux’s offensive security focus to a defensive security powerhouse. Designed for blue teams, SOC analysts, and cybersecurity defenders, Kali Purple provides an...
Read More
Kali Purple: The Ultimate Defensive Security OS – Tools & Techniques Revealed
The cybersecurity landscape is evolving, and Kali Purple has emerged as a game-changer—shifting from offensive penetration testing to proactive cyber defense. Built by the creators of Kali Linux, this new distro is packed with...
Read More
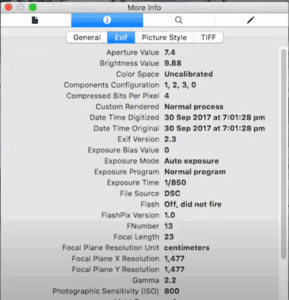
How to Extract Hidden Information from Photos Using OSINT Tools – A Detailed Guide
Have you ever thought your photos might be hiding more than just memories? In today’s digital age, images often contain layers of hidden information that can be uncovered using powerful OSINT (Open Source Intelligence)...
Read More
Uncovering Hidden Secrets in Photos: A Guide to Digital Image Forensics
Have you ever wondered what hidden information your photos might contain? Beyond what’s visible to the naked eye, images can reveal GPS locations, device details, and even personal identities—making them a goldmine for cybersecurity...
Read More
How to Enable Secure Boot in Windows 11 – A Step-by-Step Guide
If you’re looking to enhance your PC’s security and ensure your system is fully compatible with Windows 11 features, enabling Secure Boot is a smart move. Secure Boot helps protect your computer from malware...
Read More
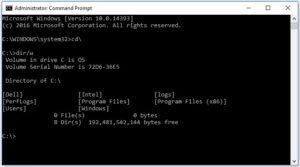
18 Powerful Windows Command Prompt Tricks You Need to Know
If you thought you were done learning Windows commands—think again. The Command Prompt (CMD) isn’t just a relic from a bygone computing era; it’s still packed with useful, powerful tools that can streamline your...
Read More
Tails OS vs Qubes OS: The Ultimate Guide to Private and Secure Browsing
If you’re someone who deeply values their privacy and security online, chances are you’ve looked into using Tails OS at some point. While it’s a powerful tool for anonymity, it isn’t the most secure...
Read More
3 Most Secure Operating Systems for Privacy-Conscious Users
Your operating system can be either your strongest shield for privacy—or your biggest vulnerability. In today’s digital landscape, using a secure operating system is crucial if you want to avoid surveillance, data leaks, and...
Read More
How to Run Tails OS from a USB Drive: Stay Anonymous and Secure Online
Imagine an operating system that offers complete online freedom—no ads, no surveillance, no censorship, and no tracking from government agencies. Now imagine this level of privacy being absolutely free, running entirely from a USB...
Read More
Understanding Reverse Engineering and Registers in Cybersecurity
In the world of cybersecurity and ethical hacking, reverse engineering is one of the most essential and challenging concepts. If you’re just beginning to explore this domain, you might wonder—what exactly is reverse engineering,...
Read More
How to Use Hydra for Brute Force Attacks on Metasploitable Using the CLI
⚠️ Disclaimer: This article is intended for educational purposes and ethical hacking only. Always ensure you have permission before attempting any penetration test. Hydra is one of the most widely used tools for performing...
Read More
A Step-by-Step Guide to Nmap Vulnerability Scanning Using NSE Scripts
⚠️ Disclaimer: This guide is intended strictly for ethical hacking and penetration testing in controlled environments with explicit permission. Do not attempt this on unauthorized systems. When it comes to penetration testing, simply identifying...
Read More
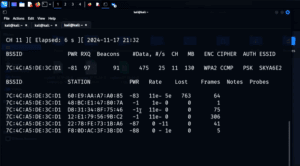
How to Capture and Crack a WPA Handshake Using Aircrack-ng (For Educational Purposes Only)
⚠️ Disclaimer: This technique is intended strictly for educational and ethical penetration testing purposes. It should never be used on public networks or without explicit permission. Always ensure you are working in a controlled...
Read More
What Kind of Person Studies Cybersecurity? Exploring the Tools, Mindset, and Teams That Shape the Field
Cybersecurity is one of the most dynamic and essential fields in today’s digital world. It’s more than just managing firewalls or writing lines of code — it’s about thinking critically, staying curious, and outsmarting...
Read More
Introduction to Shodan: The Search Engine for Internet-Connected Devices
In the world of cybersecurity and ethical hacking, Shodan is an incredibly powerful tool used to identify and analyze devices that are publicly accessible on the internet. From smart homes and business networks to...
Read More
How to Perform Reconnaissance and Vulnerability Testing Using Nikto and Nmap
In the world of cybersecurity and penetration testing, two tools stand out for their usefulness in performing reconnaissance and vulnerability assessments: Nikto and Nmap. Whether you’re a budding ethical hacker or a seasoned IT...
Read More
What Is DNS and Why It Matters: A Beginner’s Guide
Have you ever wondered how you’re able to visit your favorite websites just by typing simple names like google.com or bbc.com into your browser? Behind this convenience lies a powerful and essential component of...
Read More
Understanding Password Hashing and How to Protect Your Accounts Online
In the world of cybersecurity, protecting your password is critical. With data breaches becoming more frequent, understanding how passwords are stored and how attackers attempt to crack them is essential for both individuals and...
Read More