Java is one of the most widely used programming languages, powering applications across various platforms, including desktop, web, mobile, and embedded systems. To develop Java applications, you need the Java Development Kit (JDK), which...
Read More
A Complete Guide to Installing JDK for Java Development
Java Development Kit (JDK) is an essential toolkit for developers working with Java programming. It includes tools like the Java Runtime Environment (JRE), compiler (javac), debugger, and other utilities needed for building Java applications....
Read More
15 Essential Things to Do After Installing Fedora 33
Fedora is a robust and cutting-edge Linux distribution that’s widely appreciated by developers and tech enthusiasts. If you’ve just installed Fedora 33, there are a few critical steps you should take to ensure that...
Read More
15 Essential Things to Do After Installing Pop!_OS
Pop!_OS is a powerful, open-source Linux distribution developed by System76, based on Ubuntu and designed for a sleek and productive experience. Whether you’re a Linux newcomer or a seasoned developer, configuring Pop!_OS right after...
Read More
15 Essential Things to Do After Installing Ubuntu 20.04
Ubuntu is one of the most popular Linux distributions available today. Based on Debian, it is a user-friendly and powerful operating system suitable for both beginners and advanced users. If you’ve just completed installing...
Read More
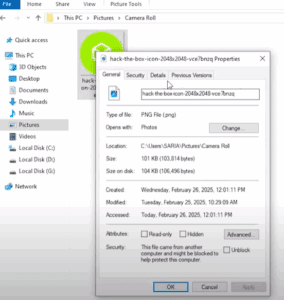
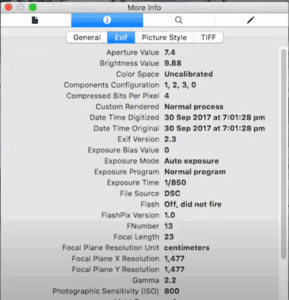
Uncovering Hidden Secrets in Photos: A Complete Guide to Image Forensics
In our digital world, every photo tells more of a story than what’s visible to the naked eye. Images contain layers of hidden data that can reveal locations, devices used, and even help identify...
Read More
How to Generate SHA1 Key in Android Studio (with Troubleshooting Tips)
If you’re working on Android app development, especially with Google APIs like Firebase or integrating login systems, one of the common requirements is to generate the SHA1 key from Android Studio. In this article,...
Read More
Top 8 Best Free Operating Systems You Can Try in 2025 – Perfect for Low-End PCs and Windows Alternatives
Are you tired of Windows slowing down your system or simply looking for a fresh and unique operating system experience? In this article, we explore eight amazing free operating systems that can breathe new...
Read More
How to Enable Secure Boot on Your PC or Laptop: Step-by-Step Guide
Secure Boot is an essential feature built into modern PCs and laptops that enhances security by ensuring that your system boots using only trusted software. Sometimes, you might need to enable Secure Boot, particularly...
Read More
Best Lightweight Linux Distributions for Your PC and Laptop
Choosing the right Linux distribution (distro) for your PC or laptop can dramatically improve your device’s performance, especially if you have a low-end or older system. In this article, we’ll explore some of the...
Read More
How to Download and Install VMware Workstation Pro for Free (2024 Guide)
Introduction VMware Workstation Pro is a powerful virtualization software that allows you to run multiple operating systems on a single Windows PC or laptop. Whether you’re a developer, IT professional, or tech enthusiast, VMware...
Read More
How to Install Ubuntu Linux 2025 on Your PC or Laptop (Step-by-Step Guide)
If you’re looking to install Ubuntu Linux 2025 on your PC or laptop, you’re at the right place! This article will guide you through the entire process, from downloading Ubuntu to creating a bootable...
Read More
How to Download and Install Linux Mint 2025: Step-by-Step Guide
Linux Mint is one of the most popular and user-friendly Linux distributions available today. With its sleek interface, robust features, and easy usability, it’s a fantastic choice for both beginners and experienced users. If...
Read More
How to Download and Install Kali Linux on VMware Workstation (Step-by-Step Guide)
If you’re planning to use Kali Linux for penetration testing or cybersecurity practice, setting it up inside a virtual machine is a smart choice. In this detailed guide, you will learn how to easily...
Read More
How to Download and Install Kali Linux on VirtualBox: A Step-by-Step Guide for Beginners
Are you interested in setting up Kali Linux on your system using VirtualBox but unsure where to start? No worries! This beginner-friendly guide will walk you through every step clearly and simply. Even if...
Read More
How to Install Kali Linux on Your PC or Laptop: Step-by-Step Guide
If you’re looking to install Kali Linux on your PC or laptop, you’re in the right place. This article will guide you through the entire process, from downloading the necessary files to setting up...
Read More
Understanding Kali Linux and Its Role in White Hat Hacking
Many of you have often asked me questions about Kali Linux — what it is, and how it is used, especially in the field of ethical hacking.Today, in this article, we’ll dive deep into...
Read More
Kali Purple: 20 Essential Post-Installation Steps for Optimal Security
Introduction Kali Purple marks a major evolution in cybersecurity tools—shifting from Kali Linux’s offensive security focus to a defensive security powerhouse. Designed for blue teams, SOC analysts, and cybersecurity defenders, Kali Purple provides an...
Read More
Kali Purple: The Ultimate Defensive Security OS – Tools & Techniques Revealed
The cybersecurity landscape is evolving, and Kali Purple has emerged as a game-changer—shifting from offensive penetration testing to proactive cyber defense. Built by the creators of Kali Linux, this new distro is packed with...
Read More
How to Extract Hidden Information from Photos Using OSINT Tools – A Detailed Guide
Have you ever thought your photos might be hiding more than just memories? In today’s digital age, images often contain layers of hidden information that can be uncovered using powerful OSINT (Open Source Intelligence)...
Read More
Uncovering Hidden Secrets in Photos: A Guide to Digital Image Forensics
Have you ever wondered what hidden information your photos might contain? Beyond what’s visible to the naked eye, images can reveal GPS locations, device details, and even personal identities—making them a goldmine for cybersecurity...
Read More