As a content creator on the internet, I frequently receive emails from various companies proposing sponsorships for my channel. Over time, reading these emails can lead to complacency, making it easier to overlook key details. Recently, I encountered a couple of suspicious sponsorship offers that serve as a cautionary tale for anyone navigating the world of online collaborations.
The “Zam” Sponsorship Email
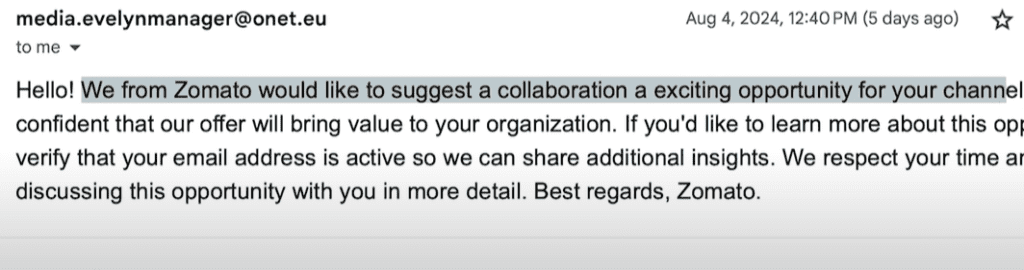
It started with an email that appeared to be a typical sponsorship request. The email stated:
“Hello, we at Zam would like to suggest a collaboration—an exciting opportunity for your channel. Kindly verify your email address so we can share additional details.”
On the surface, this seemed like a standard outreach. I confirmed my email, and they responded with a more detailed proposal:
“We aim to feature a customized 15-second Zam advertisement in your upcoming YouTube videos.”
This should have been the first red flag. According to YouTube’s terms of service, injecting ads without any commentary is not allowed. However, I brushed this off, thinking it might be a genuine mistake from a new sponsor.
The email included a link to a sample ad hosted on a seemingly official channel with significant views and subscribers. This added legitimacy to the offer. Then came the compensation details, laid out in a table—an unusual move but something I attributed to efficiency.
They directed me to review the advertising agreement through a password-protected RAR file uploaded to OneDrive. Here’s where things got interesting.
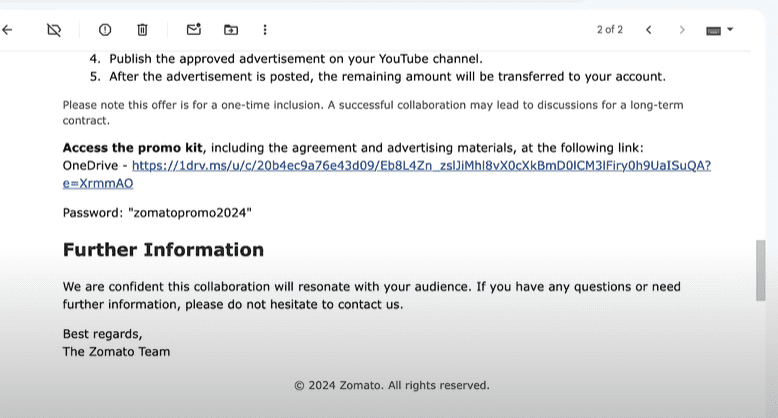
The Importance of Password-Protected Files
The password protection on the RAR file immediately raised concerns. Password protection prevents cloud services like Google Drive or OneDrive from scanning files for viruses. Knowing this, I decided to proceed with caution.
I downloaded the file on my Mac instead of my Windows PC, minimizing risk. Inside the archive was another zipped file with an ominous name: “Zamato Agreements Archive.” Extracting this revealed an EXE file—a Windows executable. This was an immediate red flag since EXE files can execute harmful programs.

Using a Virtual Machine for Safety
Before opening the EXE file, I decided to use a virtual machine (VM). For those unfamiliar, a VM is like a computer within your computer. It isolates your main system from any potential threats.
Using VirtualBox, I booted up a Windows virtual machine, disabled the shared clipboard (to prevent malware from escaping the VM), and proceeded to open the file. Sure enough, my antivirus flagged it as a Trojan virus. Since I was in a VM, deleting the infected files and restoring a clean state was straightforward. Without a VM, this virus could have compromised my actual computer, causing significant damage.
A Second Suspicious Email: Sony Vegas Scam
A few days later, I received another email, this time claiming to be from Sony Vegas:
“Greetings, dear social partner. Our team finds your content suitable for an integration into our product.”
This email seemed plausible, especially since I had recently reviewed a competing video editing software. However, there were subtle warning signs, like placeholders in the text (e.g., “{recipient’s name}”) and the domain of the provided link (“vegascreativesoftware.com.pl”). The “.pl” indicated that this was not the official website.
Again, they provided a password-protected ZIP file containing another suspicious EXE file. Following the same process, I used a VM to investigate. The EXE file triggered antivirus warnings, confirming it was another Trojan.
Lessons Learned and Best Practices
These incidents highlight how easy it is to fall for seemingly legitimate offers when you’re not vigilant. Here are the key takeaways:
- Verify Email Domains: Always check the domain of the sender’s email and any links provided. Legitimate companies will use official domains.
- Be Wary of Password-Protected Files: Password protection can hide malicious content from virus scanners.
- Use a Virtual Machine: A VM is an invaluable tool for safely investigating suspicious files or websites. It allows you to isolate potential threats from your main system.
- Pay Attention to Details: Look for inconsistencies in language, placeholders, or unusual file formats.
- Enable Antivirus Software: Keep your antivirus software active and updated to catch threats in real time.
Setting Up a Virtual Machine
If you want to set up a virtual machine for added security, here’s a quick guide:
- Download VirtualBox: Install the free VirtualBox software from its official website.
- Download an Operating System (OS): For Windows, download the ISO file from Microsoft’s official site.
- Create a New VM: Open VirtualBox, click “New,” and follow the prompts. Allocate less than half of your computer’s resources to the VM.
- Install the OS: Select the downloaded ISO file and proceed with the installation.
- Clone the VM: Once set up, clone the VM to have a clean backup ready for future use.
Final Thoughts
Even seasoned creators can fall victim to scams if they’re not careful. By staying vigilant and using tools like virtual machines, you can protect yourself from malicious actors. Remember, it’s better to be overly cautious than to risk compromising your system.
Tags: online scams, email scams, virtual machine tutorial, cybersecurity tips, sponsorship scams, content creator tips
Hashtags: #Cybersecurity #VirtualMachine #SponsorshipScams #ContentCreators #OnlineSafety