Creating reusable blocks—also known as patterns—in WordPress is a great way to save time and maintain consistency across your content. Whether it’s a styled button, a section layout, or a call-to-action, reusable blocks can...
Read More
🙌 How to Set Up a Donation Page and Add a Donate Button in WordPress (Step-by-Step)
If you’re looking to collect donations through your WordPress website, you’re in the right place. Whether you’re an individual, non-profit, or organization, setting up a donation page and adding a Donate button is easier...
Read More
✅ How to Safely Downgrade Your WordPress Version Without Breaking Your Site
There may be times when a WordPress update introduces bugs or conflicts with your themes and plugins. In such cases, downgrading to a previous version can be a quick fix until a compatible update...
Read More
How to Use Gemini AI to Analyze Videos and Build Applications in Python
AI is evolving at lightning speed, and one of the most exciting developments right now is Gemini’s multimodal capabilities. Among the top large language models (LLMs), Gemini currently stands out as the only one...
Read More
AI Agents: The Next Evolution in Artificial Intelligence
Artificial Intelligence is rapidly evolving, and one of the most significant recent advancements is the emergence of AI agents. These systems represent a major leap forward from traditional large language models (LLMs), enabling machines...
Read More
10 Riddle Questions That’ll Put Your Brain to the Test
Are you ready to challenge your brain and have some fun along the way? This article presents a set of 10 clever riddles that test your logical thinking, memory, and problem-solving skills. Each question...
Read More
How to Use Hydra for Brute Force Attacks on Metasploitable Using the CLI
⚠️ Disclaimer: This article is intended for educational purposes and ethical hacking only. Always ensure you have permission before attempting any penetration test. Hydra is one of the most widely used tools for performing...
Read More
A Step-by-Step Guide to Nmap Vulnerability Scanning Using NSE Scripts
⚠️ Disclaimer: This guide is intended strictly for ethical hacking and penetration testing in controlled environments with explicit permission. Do not attempt this on unauthorized systems. When it comes to penetration testing, simply identifying...
Read More
How to Capture and Crack a WPA Handshake Using Aircrack-ng (For Educational Purposes Only)
⚠️ Disclaimer: This technique is intended strictly for educational and ethical penetration testing purposes. It should never be used on public networks or without explicit permission. Always ensure you are working in a controlled...
Read More
What Kind of Person Studies Cybersecurity? Exploring the Tools, Mindset, and Teams That Shape the Field
Cybersecurity is one of the most dynamic and essential fields in today’s digital world. It’s more than just managing firewalls or writing lines of code — it’s about thinking critically, staying curious, and outsmarting...
Read More
Introduction to Shodan: The Search Engine for Internet-Connected Devices
In the world of cybersecurity and ethical hacking, Shodan is an incredibly powerful tool used to identify and analyze devices that are publicly accessible on the internet. From smart homes and business networks to...
Read More
How to Perform Reconnaissance and Vulnerability Testing Using Nikto and Nmap
In the world of cybersecurity and penetration testing, two tools stand out for their usefulness in performing reconnaissance and vulnerability assessments: Nikto and Nmap. Whether you’re a budding ethical hacker or a seasoned IT...
Read More
What Is DNS and Why It Matters: A Beginner’s Guide
Have you ever wondered how you’re able to visit your favorite websites just by typing simple names like google.com or bbc.com into your browser? Behind this convenience lies a powerful and essential component of...
Read More
How to Download and Install Arch Linux on VirtualBox: A Step-by-Step Guide
Arch Linux is known for being a flexible, minimalist distribution that gives users complete control over their setup. If you’re ready to explore this powerful Linux distro but want to test it first in...
Read More
Understanding Password Hashing and How to Protect Your Accounts Online
In the world of cybersecurity, protecting your password is critical. With data breaches becoming more frequent, understanding how passwords are stored and how attackers attempt to crack them is essential for both individuals and...
Read More
How to Install Kali Linux on a USB Flash Drive: A Step-by-Step Guide
Disclaimer:This article is intended for educational purposes only. The tools and techniques discussed here should only be used ethically and legally, never for any malicious or unauthorized activity. Installing Kali Linux on a USB...
Read More
How to Perform Wi-Fi Penetration Testing Using Fern and Wifite on Kali Linux
Disclaimer:This article is intended strictly for educational purposes only. The tools and techniques described here are designed for ethical hacking and cybersecurity learning. Never attempt unauthorized access to any network you do not own...
Read More
A Beginner’s Guide to Computer Networking: From IP Addressing to NAT
Have you ever wondered how computers communicate with each other across the globe? It might seem like magic, but in reality, it’s a well-orchestrated system known as computer networking—a complex yet fascinating field that...
Read More
Introduction to BetterCAP: The Swiss Army Knife for Network Penetration Testing
Disclaimer: This article is for educational purposes only. The techniques and tools described should never be used on public networks or without proper authorization. Always ensure your actions comply with applicable laws and ethical...
Read More
Understanding Hashing and Encryption: A Beginner-Friendly Guide
In today’s digital age, security and privacy are top priorities. Whether you’re creating an online account or sending confidential messages, cryptographic concepts like hashing and encryption play a crucial role in safeguarding your data....
Read More
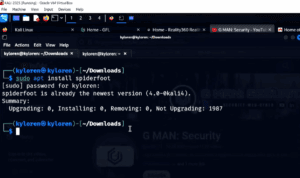
How to Use SpiderFoot with GUI on Linux for Ethical Hacking and Vulnerability Scanning
SpiderFoot is a powerful open-source OSINT (Open Source Intelligence) tool used to automate the process of gathering information about IP addresses, domains, emails, and more. It’s perfect for penetration testers, cybersecurity professionals, and ethical...
Read More